Four years ago, Dropbox was hacked. At the time, public information said that only email addresses were stolen. We now know a copy of users’ encrypted passwords were also taken. Knowing that your information could be compromised, what should you do to protect yourself?
Since the stolen passwords were appropriately encrypted, instead of the hackers seeing plain text passwords, they were instead greeted with a series of seemingly random characters. For you , this means one of two things:
- If you use a strong password, it is extremely unlikely anyone is going to be able to decrypt it during your lifetime.
- If you don’t use a strong password — something really simple like “letmein” — and someone took the time to try to get into your account, they could brute force their way to revealing your password very quickly.
If you are in camp #1, it would take considerable effort and time to crack a reasonably strong password. The quality of the password used to protect the account and the resources of the attacker play a big role in how long it would take to crack these kinds of passwords. For most reasonable passwords and typical attacker resources, this is in the hundreds or thousands of years time frame to crack.
Even if someone like China, with their fancy super computers, has a deep interest in your documents AND they are willing to spend years cracking a password, it’s not going to matter, because the encryption is powerful. Even with their advanced technology, if the password is rock-solid, they probably still won’t have the means to crack it.
If you are in camp #2, Dropbox already notified you and reset your password. Take the extra step of changing that bad password into a good one, and be sure to change it on any other sites you may have used it on. This is especially important for email accounts, as someone with access to your email account can reset passwords for other sites.
Weak passwords such as “Password1” and “letmein” (short passwords based on dictionary words) are much easier to crack. The best passwords are actually password phrases that use unrelated words together. Something like fancymarsduckspartan contains 20 characters but is easy to remember.
For example, this is how long it would take to hack fancymarsduckspartan:
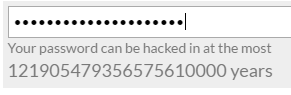
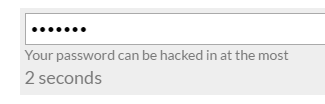
While “letmein” can be hacked in a matter of seconds:
To find out how great of a password you’ve come up with, you can test yours using a password strength test utility.
Even better than strong passwords alone is enabling two-factor authentication (2FA) for Dropbox. Using this means that even if the login is stolen, no one can get into your Dropbox data unless they also have your physical cell phone or other authenticating device. It’s called two-factor authentication because in order to access the account you need both something you know (your password) and something you have (your phone).
Using two-factor authentication along with secure passwords negates most of the risk associated with using an online service. If you need some help getting started, check out Dropbox’s help page on using two-factor authentication with their service.
Every breach of a major company like this highlights the importance of proper password security, especially the fundamentals:
- Use strong passwords for every website. Do not compromise on password security just because a site doesn’t seem important.
- Do not using the same password across multiple sites. This ensures that if one site is compromised, the attackers can’t try that password on your other accounts. A Password manager like LastPass or 1Password can help you with this.
- Use two factor authentication — if you only take one action after reading this article, make it integrating 2FA into your accounts! Check out Two Factor Auth for more sites and services that support this secure option.
What happened to Dropbox can and does happen to other companies. It will happen again. Be prepared!
If your business needs help with online security, we are here to help!