In our roundup of vital security practices, we mentioned using a VPN to encrypt your network traffic. Now, we want to go deeper and explain what a VPN does, why you should use one, and how to get one.
Let’s look at what a VPN offers and how you can integrate one into your workflow.
What Is a VPN?
VPN stands for virtual private network. Essentially, it allows you to connect to a private network over a public internet connection. There are two main types of VPNs.
The first is a business VPN, which enables you to access resources on your company network no matter where you are. For example, when you’re at home, you can’t access files on a company server because you aren’t on that closed network. A VPN allows you to connect to your work’s network, no mater where you are, and work as if you’re actually there.
The other common kind of VPN is one used for privacy. You’ll find many online VPN services that let you connect to their servers to protect your browsing. We’ll look at these more in-depth in a bit.
No matter the specifics of the VPN you use, the important part is that it enables you to connect to a private network, even if you’re not physically on it.
Why Should I Use a VPN?
You might wonder what the point of a VPN is. As we’ve mentioned, business users can take advantage of VPNs to get on their work network from anywhere. If they forgot to grab a file stored on a company server, or need to access an internal website from home, they can just fire up their VPN and connect.
But there are several reasons to use a VPN, even if you don’t need it for business.
Privacy
The biggest reason to use a VPN is privacy. As you probably know, multiple entities track what you do online. Whether it’s an advertiser trying to figure out how to show you better ads, companies like Google using your data to improve their services, or a government, what you do online is far from private.
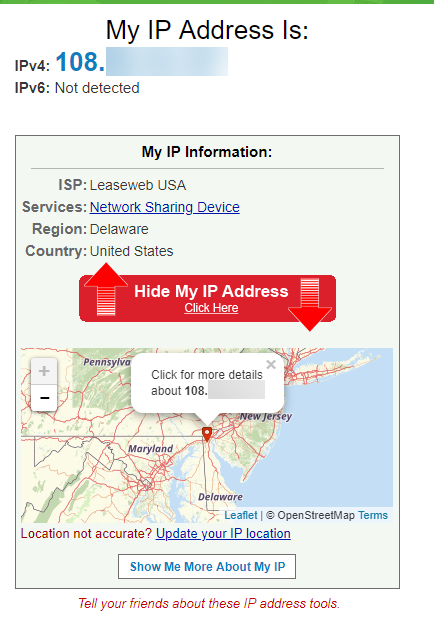
As an example, visit a site like What Is My IP Address and you’ll see how much data can be gleaned about your browsing. Anything online can see your IP address, which reveals your general location, ISP, and more.
Security
Another important use of a VPN is to protect you on insecure networks. We’ve looked at why public Wi-Fi isn’t secure (like networks in coffee shops and airports) before. Because these connections are open and not encrypted, anyone can connect and view what you’re doing.
Connecting to a VPN encrypts your activity between your device and the VPN provider. Thus, if someone intercepted your browsing data at Starbucks while you were on a VPN, they would only get gibberish.
How to Start Using a VPN
There’s no shortage of VPN services you can sign up for. Which one you choose depends on a variety of factors. Remember that you’re trusting all your browsing data to a VPN provider, so it’s important to choose carefully.
Avoid Free VPNS
First, we don’t recommend using a free VPN if you can help it. As the saying goes, if you’re not paying for something, you’re the product. Free VPNs have to make money somehow, and many of show annoying ads or sell your browsing data. This completely defeats the point of using a VPN.
Worse yet, some free VPNs are dangerous. They might expose your devices to malware. This is the case with the free Hola VPN, which was essentially acting as a giant botnet of users.
Log History and Country of Operation
Next, you should make sure your VPN has a no-logs policy. Some VPNs keep logs of their users’ browsing, which again is totally contrary to why you want to use a VPN in the first place.
Finally, you should also check which country the VPN provider is based in. Governments in several countries are infamous for forming alliances to perform surveillance on their citizens, swap surveillance information with other countries, or otherwise spy on people.
They are:
- Five Eyes countries: United States, United Kingdom, Canada, Australia, and New Zealand.
- This alliance goes all the way back to the end of World War II. In Edward Snowden’s infamous leaks, much of the information pertained to global surveillance by these five countries. Each country has strong authority to force a company to hand over data.
- Nine Eyes countries: the above, plus Denmark, France, the Netherlands, and Norway.
- These are essentially extensions of the main Five Eyes countries. It’s not fully known what separates them, but it’s fair to say their partnership is not as close (not all these countries speak English like the Five Eyes do). But they’re still comfortable with sharing data with the Five Eyes.
- Fourteen eyes countries: all of the above, plus Belgium, Germany, Italy, Spain, and Sweden.
- The Snowden leaks confirmed another agreement among these 14 nations. It’s known as SSEUR, or Signals Intelligence Seniors Europe. Again, they’re not as close as the Five Eyes, but are comfortable sharing information.
Companies located in one of these regions could potentially be forced to turn over sensitive information about their users. Trusted VPN provider Private Internet Access explained why they don’t feel this is an issue, but it’s still something to consider.
Recommended VPNs
In case you’re not sure how to proceed, here are a few quality VPNs we recommend:
- ExpressVPN: This VPN has no limitations, is based in the British Virgin Islands, and has plenty of security features.
- NordVPN: Located in Panama, keeps no logs, and offers affordable plans.
- Private Internet Access: Good all-around balanced VPN.
- CyberGhost: Offers tons of servers, keeps no logs, located in Romania, and offers installation guides for many devices.
There are other solid VPNs, but these are all good choices to start with.
After you sign up for one of them, you just need to install the app on your phone, computer, and other devices. From there, you can sign into your account and connect to any server you like. Once connected, all your browsing data will be protected.
Start Using a VPN Today
We’ve looked at the value a VPN offers, how the work, and a few tips for picking a good one. Hopefully you now understand VPNs better and might start using one yourself.